Xplico 1.1.2: CapAnalysis
 As some of you might know CapAnalysis is open source. To analyze the pcap files CapAnalysis uses Xplico with some specific dissectors.
As some of you might know CapAnalysis is open source. To analyze the pcap files CapAnalysis uses Xplico with some specific dissectors.
With this release of Xplico we complete the open source migration of CapAnalysis.
Everyone can use CapAnalysis not only by installing it but also by freely using it from the demo site. The demo gives the possibility to upload up to 20MB of PCAP files. No password is required and all data are deleted automatically at 00:00 UTC the day after the creation of dataset.
From the point of view of Xplico users this release doesn’t introduce new features.
The code can be found on GitHub.
Xplico 1.0.0 Released
Xplico 1.0.0 is now available!
ChangeLog:
- SQLite dispatcher performance improved
- added the PPI dissector
- added the syslog dissector
- added “Bogus IP length” correction with checksum verification disabled
- new Facebook Chat dissector for the new Facebook chat protocol
- SIP dissector improved
- IMAP dissector improved and bugs fixed
- DNS dissector PIPI improved
- Yahoo Webmail bugs fixed
- Live/Hotmail WebMail Spanish version
- GeoMap improved
- PCap-over-IP
Xplico Repository (Ubuntu 11.04 or higher)
To install Xplico in your Ubuntu Server or in your Desktop now you can use the official Xplico repository. With four simple steps you can have Xplico running and updated.
sudo bash -c 'echo "deb http://repo.xplico.org/ $(lsb_release -s -c) main" >> /etc/apt/sources.list'
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 791C25CE
sudo apt-get update
sudo apt-get install xplico
Thanks
- Stack Overflow users.
- Erika Noerenberg for her analysis in the post “Brief overview of 4 NFATs”
- Victor Oppleman to suggest us to add PCap-over-IP
Web Demo
We are completing the tests on 0.7.0 version. In this release the main features are:
- Gmail Webmail (HTTP)
- Yahoo! Mobile Mail (Andorid)
- AOL WebMail (last version)
- Language localization
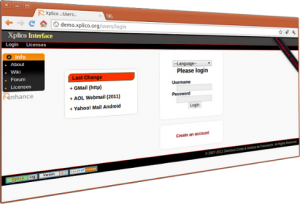
The “WebMail sniffer” component (manipulator and python scripts) were improved.
All this features and others can be examined and tested with the Web Demo of Xplico.
Any help on Language translation and bug report or suggestions are greatly appreciated.
In the Web Demo all data can be remove by you, in anyway all data (but not the users accounts) are removed every day at 00:00 UTC. More info about Web Demo can be found here.
Xplico 0.6.2: l7-patterns
This version introduces l7-patterns classifier for all flows not decoded, also there is the improvement of the real time acquisition, new features for the XI (Xplico Interface) and many bugs fixes.
ChangeLog:
- l7-patterns for all flows/protocols not decoded by xplico
- Xplico Interface (XI) improved
- python3 porting of many scripts
- realtime capture module improved
- facebook chat realtime view
- UTC/localtime bug fixes
- l2tp dissector bug fixes
- cli and lite dispatchers bug fixes
- telnet dissector bug fixes
- trigcap bug fixes
- new script named session_mng.pyc to facilitate the creation of new case and/or new session from command line
We thank naif for his support and his availability.
The decoding performance are:
- from command line: 5.9 MB/s
- from Xplico Interface (XI) with SQLite DB (=> lite dispatcher): 1.76 MB/s
- from Xplico Interface with MySQL DB (=> ximysql dispatcher): 4.09 MB/s
measured on an Aspire 5633WLMi (Intel Core 2 Duo processor T5500 with 1GB RAM an HD IDE controller) with the pcap http://domex.nps.edu/corp/scenarios/2009-m57/net/day11-18.dmp.zip (851 MB).
As always: Enjoy !
Xplico version 0.5.5: WebMail
In this version:
- migrating to SQLite3
- telnet dissector
- webmail dissector
- webmail manipulator: Yahoo!, AOL, Hotmail (all without attachments)
- Improved LLC dissector
- Improved XI
- script to check new release (only in source code)
Hotmail (Live) depends on the language. Currently the languages supported are Italian and English.
Any feedback are welcome: forum.
You can download VirtualBox image, source code and Ubuntu 9.10 package here.
Forensic challenges
Currently there are at least 2 Forensic challenges in which Xplico can be used and can facilitate the analysis. These two challenges are:
We do not answer the questions, here we will give some indication of use of Xplico.
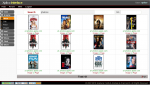
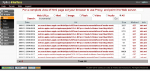
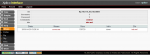
The “Ann’s AppleTV” pcap file has no particular problems of decoding, in fact if you process the pcap you obtain the data represented in the two pictures below.
For the “Forensic Challenge 2010 – pcap attack trace” pcap decoding requires more attention. In fact this pcap file has corrupted packet (and not retransmitted), so you must disable the Xplico checksum verification (HowTo).
From cli the command is:
./xplico -c config/xplico_cli_nc.cfg -m pcap -f attack-trace.pcap
Since Xplico is able to recognize the protocols (not all) even if they use non-standard ports is easy to see what protocol was used and which data file was downloaded.
In the figure below there is the result of decoding with XI.
Enjoy ;).
Xplico version 0.5.4: Facebook Chat
This version of Xplico introduce new and important features:
- Facebook web chat dissector
- New XI based on CakePHP 1.2.5
- New representation of images
- For each image you can see (with the proxy enabled) the page where the image is contained
- WLAN and LLC basic dissectors
- HTTP dissector Improvements
You can download source code, Ubuntu 9.10 package and VirtualBox.org image here.
Xplico version 0.5.3 and DEFT Vx5
You can find this release in DEFT Vx5 Linux distribution.
You can download source code, Ubuntu 9.10 package and VirtualBox.org image here.
This version of Xplico introduce many new features:
- snoop Packet Capture File Format as input file
- DNS dissector with graphical representation in Xplico Interface (XI)
- NNTP dissector
- PPPOE dissector
- direct live acquisition from XI
- new dispatcher named CLI: this dispatcher organize the data extracted in a tree as this:
xdecode/<ip_src_1>/http
xdecode/<ip_src_1>/mail/
xdecode/<ip_src_1>/nntp
xdecode/<ip_src_1>/ftp
xdecode/<ip_src_1>/...
xdecode/<ip_src_2>/http
xdecode/<ip_src_2>/mail/
xdecode/<ip_src_2>/nntp
xdecode/<ip_src_2>/ftp
xdecode/<ip_src_2>/...
- default CLI dispatcher in command line execution
- file extension for the HTTP contents
We have to thank:
- Carlos Gacimartín, for his help
- Doriano Azzena, for his support in debugging
- Matteo G.P. Flora for inspiration of DNS XI graphics
- Open Flash Chart team for their wonderful tool
- all forum users for their debug
Enjoy ;).
MMS and GeoMap version
This release introduce the MMS dissector. With this dissector it is possible to reconstruct the MMS message transported by HTTP protocol and extracts the media contained. With the new release of Web interface it is possible to view photos, texts and videos contained in MMS messages.
In this release of Xplico we have introduced the generations of geographical and temporal map of data rebuilding by Xplico. This feature named GeoMap can be used both with console mode and Web interface. The files generated by GeoMap are kml files an can be used with Google Earth. To allow the visualization of the connections whose source is a private IP address, we have decided that the private IP address are located in Venice (this is a temporary solution).
We have to thank:
- Collin Richard Mulliner for your mms messages
- Kowsik Guruswamy for your Cap’r Makr’ tool, and for your very fast support
- SecViz for inspiration of GeoMap
- MaxMin for your open source GeoIP library
- Wireshark team for… ALL
An example of MMS over HTTP you can find here.This pcap was generated with Cap’r Makr’ and with the mms of Flavio Poletti.
Any bug reports or suggestions are welcome.
Gmail visualization from pcap capture
If you sniff, with tcpdump or other tools, all Gmail traffic (before login) and you give this capture to Xplico using Web interface, then you can view the emails of Gmail, even if you have not read the email (this is true only for the first emails on the list).
Obviously, before capture the Gmail traffic, you must clean the cache of Firefox to force the download of all contents, this to allow Xplico to rebuild all data.
The Web interface (PHP code) is necessary and it is also necessary:
- to use Firefox in the same machine where is Web interface (Apache)
- to enable proxy in Firefox (HTTP porxy: localhost Port: 80).
You can use DEFT (v3x, v4, …) to test this feature.
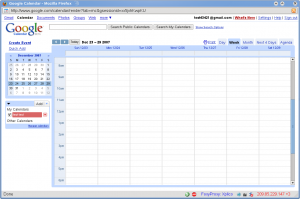
Even Google Calendar can be rebuilt with Xplico. In this screenshot you can view an example, obtained from the pcap file extracted from gmail.com.pcap.e01 archive of PyFlag project.
This feature is experimental and it is in development. Now the engine is written in PHP but we are developing an engine in C with many more features.